Whilst the Internet does bring a lot of wonderful things, it also presents a number of security challenges for consumers and businesses of all sizes, especially when it comes to keeping sensitive information secure. One of the key threats we face is ‘phishing’ a form of cyber-attack. Each time a purchase is made via the web, or we access our bank and credit card accounts, we enter information hackers love to get their hands on!
As a business, especially those in the eCommerce arena, first of all you can build confidence with your customers by moving your website to HTTPS, by adding SSL encryption. Please take a look at this earlier article for more information. You can also employ a two-stage authentication process for any customer accounts where you provide access online.
Here are 3 of the most common phishing methods fraudsters or hackers use to try and trick you into disclosing personal data.
According to a report from PhishMe1 (based on survey data collected during 2015/16), 91% of cyber attacks start with a phish.
1) Fake phishing emails
Business or home users often find it difficult to differentiate a phishing email from genuine, normal mail because they look so similar. As a basic rule, think twice before clicking on any links included within mails received from a person or business you don’t know.
Fake emails are designed to entice you to take certain action e.g. verify your details, or visit a fake web page to confirm or dispute something. Most of the time these links are specifically created to steal your passwords or login information.
The top 3 reasons (according to the PhishMe survey) people are fooled by phishing emails are:
- curiosity (13.7%)
- fear (13.4%)
- urgency (13.2%)
This is a screen shot of an email I recently received – it’s a prime example of phishing.
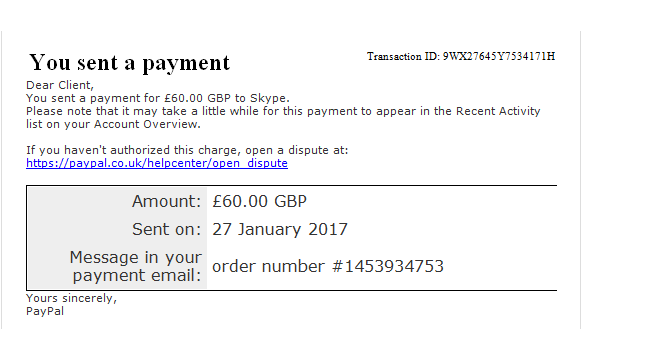
It purports to come from PayPal and fits perfectly into the fear / urgency phishing category. The email is designed to make me act on impulse. I immediately know the transaction isn’t real – the fraudster is trying to trick me into clicking on a link, to go to a web page where I will be asked to enter my paypal log in details. If I do this they will capture my login details for this financial organisation, immediately opening my account up to fraud – IT IS AS SIMPLE AS THAT!
One thing to note here is that the email is addressed to ‘Dear Client’ – you will see this a lot in fake emails. Your supplier will know your name, so why have they not used it? Treat situations like this as an immediate red flag.
The websites you are sent to can be really convincing – they will duplicate the real business website detail by detail, including the logo, so it can be really hard to spot it’s a fake.
If I receive any unexpected emails, particularly from financial institutions I deal with, I NEVER click on any of the links in the email. Most of the time I just delete them, however, if I think there could possibly be an issue I need to investigate, I will either call them, or go to MY USUAL method of logging in, e.g. by typing the URL in manually and see if there are any account messages for me.
In some cases, you can hover your mouse over the links in an email & you get a small pop up showing the real destination of the link, or over the sender email, to see the details of the real sender. Thankfully, most phishing mails can easily be identified by doing this. The official domain of a reputable company is close to impossible to recreate, so the phishers create dummy domains whose address looks similar to the one used by the other companies, but it’s not the same.
As a business, you can help further by making it clear to your customers how you will get in touch should you need to notify them about an unexpected account related matter. If you do need to send out emails, always use their name and suggest that they log into their account by manually typing in your business URL, rather than including a link. Alternatively call them, but never ask them to verify their contact details when YOU CALL THEM.
2) Attaching a trojan to an email
A Trojan is malicious software which can be sent as an attachment to an email. If you do not have anti-virus software installed (which is also regularly kept updated) a Trojan can sometimes unknowingly install itself onto your computer & steal data, by monitoring your general activities, including the ability to capture log in information for websites.
As a business owner use reputable business malware protection and educate your staff. Check out this article for more information.
3) Phone calls
Some unscrupulous people can phone you pretending to be one of your ‘suppliers’ and try and trick you into revealing sensitive information. I have seen television programmes about this. Con artists of this nature make it look incredibly simple!
A few big businesses are currently running TV awareness campaigns specifically showing you how it can be done. As a business owner, you can reassure your customers that if you call them, you will not ask them to reveal any ‘security information’ to confirm who you are.
Remember, trust your gut feel – if it doesn’t feel right – it’s probably fake.